VoLTE Traffic Model & VoLTE Bearers(Training Session#1)
This training session focuses on 4G & 5G voice services, 𝗶𝗻𝗰𝗹𝘂𝗱𝗶𝗻𝗴 𝗩𝗼𝗡𝗥, 𝗩𝗼𝗟𝗧𝗘, 𝗮𝗻𝗱 𝗘𝗣𝗦 𝗙𝗮𝗹𝗹𝗯𝗮𝗰𝗸. The comprehensive End-to-End (E2E) VoLTE Training will cover an overview of VoLTE, including traffic models, IMS architecture, end-to-end call flow analysis using logs, and main features. 𝗜𝗻 𝘁𝗵𝗶𝘀 𝘃𝗶𝗱𝗲𝗼, 𝘄𝗲 𝘄𝗶𝗹𝗹 𝗰𝗼𝘃𝗲𝗿 𝘁𝗵𝗲 𝗳𝗼𝗹𝗹𝗼𝘄𝗶𝗻𝗴 𝘁𝗼𝗽𝗶𝗰𝘀:
1- Introduction(Contents)
2- VoLTE Introduction Overview
3- Traffic Model Scheme and Speech Codec
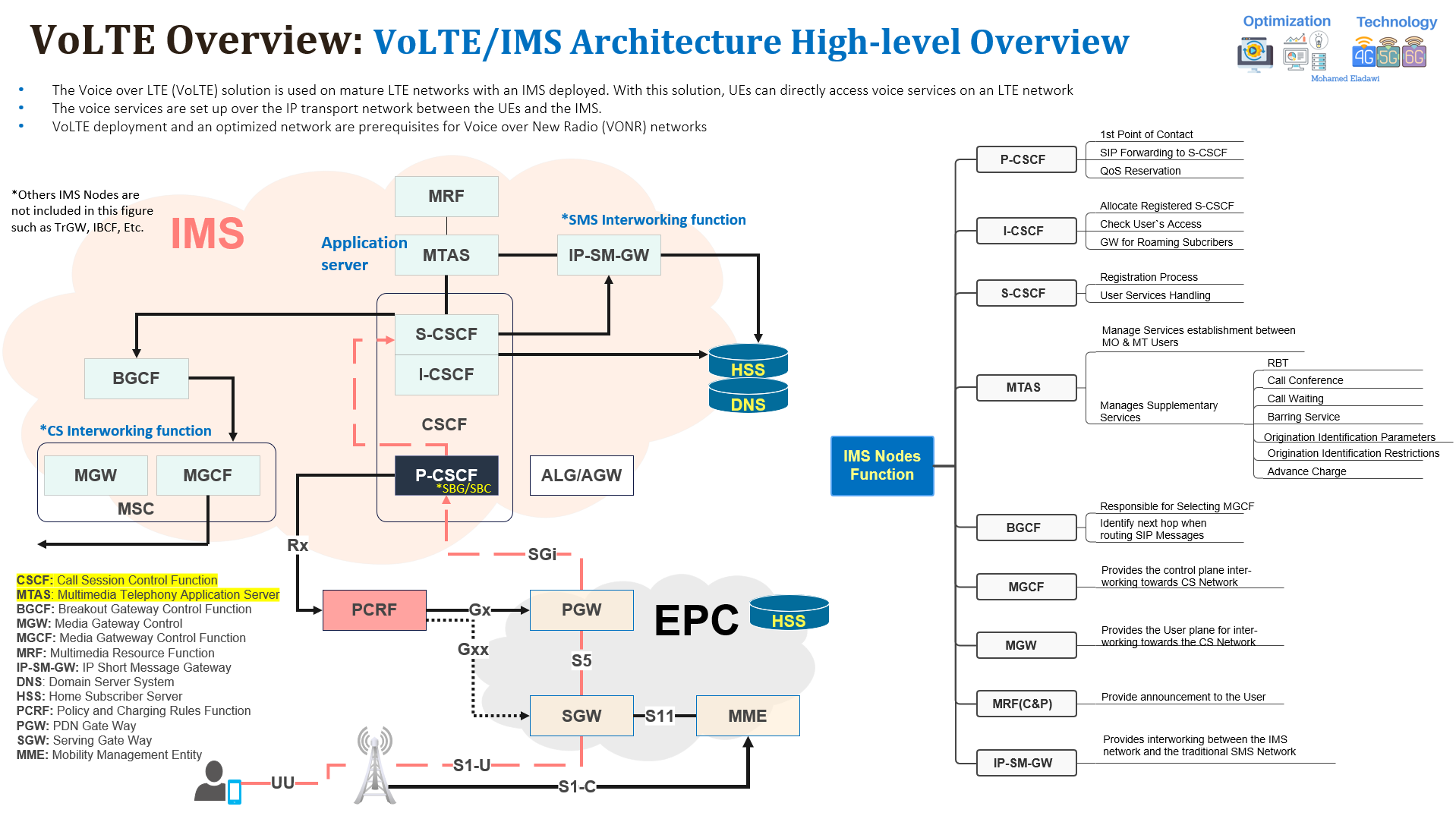
4- High-level Overview of VoLTE/IMS Architecture
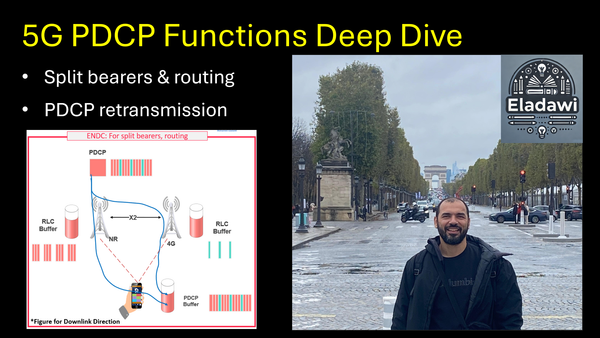
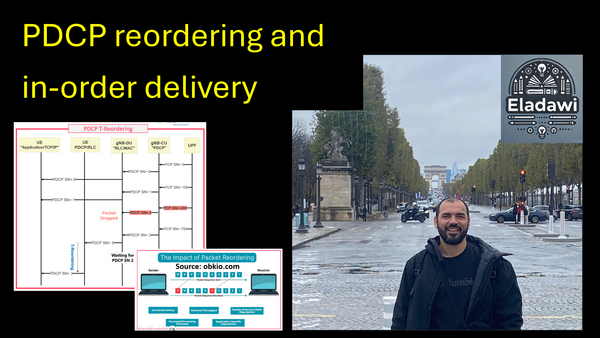
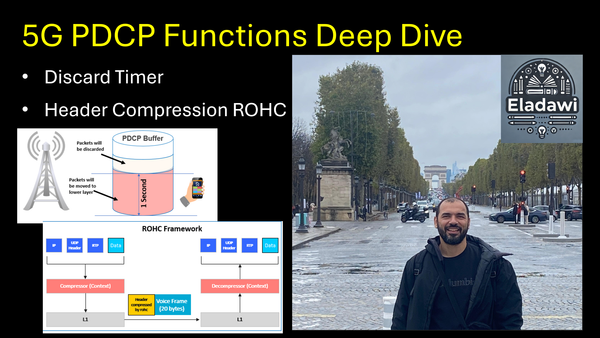
5- VoLTE Bearers and Protocols
6- High-Level VoLTE Call Procedures